Security
Asus Router Vulnerability: Thousands of Devices Hacked in Stealthy Cyberattack
In May 2025, cybersecurity researchers discovered a sophisticated and ongoing campaign exploiting an Asus router vulnerability. This large-scale operation has compromised thousands of devices and turned them into part of a malicious proxy network. Attackers have hacked Asus routers by leveraging multiple previously patched vulnerabilities to install persistent backdoors that allow remote control. Scope of the Attack: Over 9,000 Routers Compromised According to data observed by GreyNoise, more than 9,000...
10 Proven Tips to Boost Your Home Network Security in 2025
Your home network is the digital front door to your life. From remote work and online banking to smart home controls and streaming, everything connects through your Wi-Fi. But as our lives get more connected, they also become more vulnerable. Cybercriminals are constantly evolving their tactics to exploit weak points in home setups. You don’t need to be a professional to care about your home network security — it’s something...
AirPlay Vulnerability Exposes Billions of Apple Devices to Remote Attacks
A newly disclosed AirPlay vulnerability, also referred to as the AirBorne vulnerability, in Apple’s AirPlay protocol and software development kit (SDK) exposes billions of devices—including iPhones, iPads, Macs, Apple TVs, smart speakers, and even CarPlay-enabled infotainment systems—to serious security risks. Discovered by researchers at Oligo Security, these flaws enable a range of cyberattacks, from remote code execution (RCE) and data theft to full-scale surveillance. What Is the AirPlay Vulnerability? Oligo...
Who’s on Your WiFi? How to See and Block Unauthorized Users
Is your internet running slower than usual? Are you noticing unusual activity on your network? If so, you might be wondering, who is accessing my WiFi? Unwanted users can slow down your connection, compromise your security, and even put your personal data at risk. Fortunately, there are simple ways to check who’s on your WiFi and take action to secure your network. Let’s go through the best methods to identify...
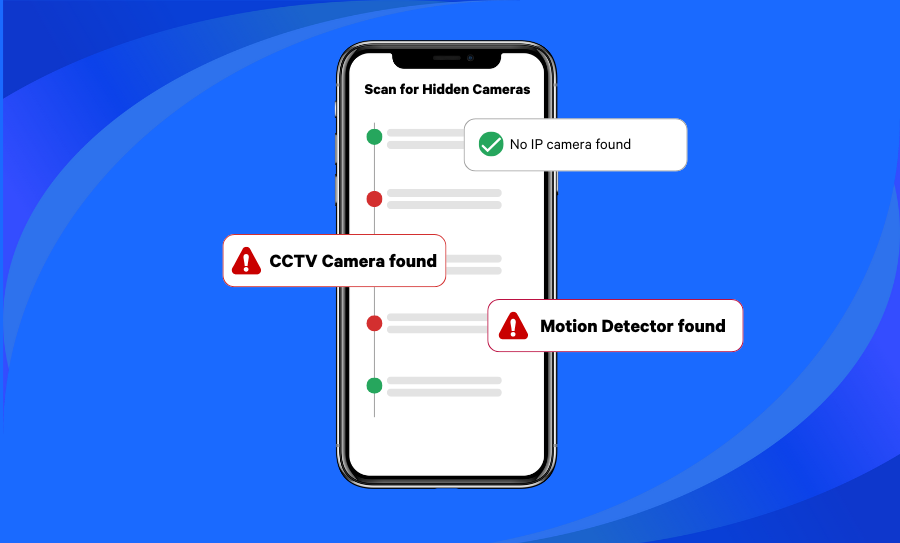
How to Find Hidden Cameras: A Guide for Airbnb and Other Rentals
Staying in an Airbnb rental can offer a unique and personal travel experience, but it’s essential to ensure your privacy and safety. One of the growing concerns for travelers is the potential presence of hidden cameras. The thought of being secretly watched in an Airbnb or hotel room is enough to make anyone uneasy. Whether you’re staying in a short-term rental or private accommodation, it’s important to know how to...
New PolarEgde Botnet Targets NAS and Router Vulnerabilities in Major Brands
TL;DR: PolarEdge is a newly discovered IoT botnet targeting devices from major brands like Cisco, ASUS, QNAP, and Synology. It exploits vulnerabilities, such as CVE-2023-20118 for Cisco Routers, using cloud services to spread malicious payloads. Over 2,000 devices have been compromised globally, posing risks of DDoS attacks, spam campaigns, and malware distribution. Unveiling PolarEdge: The Emerging IoT Botnet Threat In recent months, cybersecurity experts have uncovered a previously undocumented IoT...
How to forget a network on Mac in 7 steps
Is your Mac automatically connecting to a Wi-Fi network you no longer want to use? Do you need to forget a hotel Wi-Fi or a network with a changed password? Whatever the reason, learning how to forget a network on Mac ensures you have full control over your Wi-Fi connections. In this guide, we’ll walk you through the exact steps to remove a Wi-Fi network from your Mac, along with...
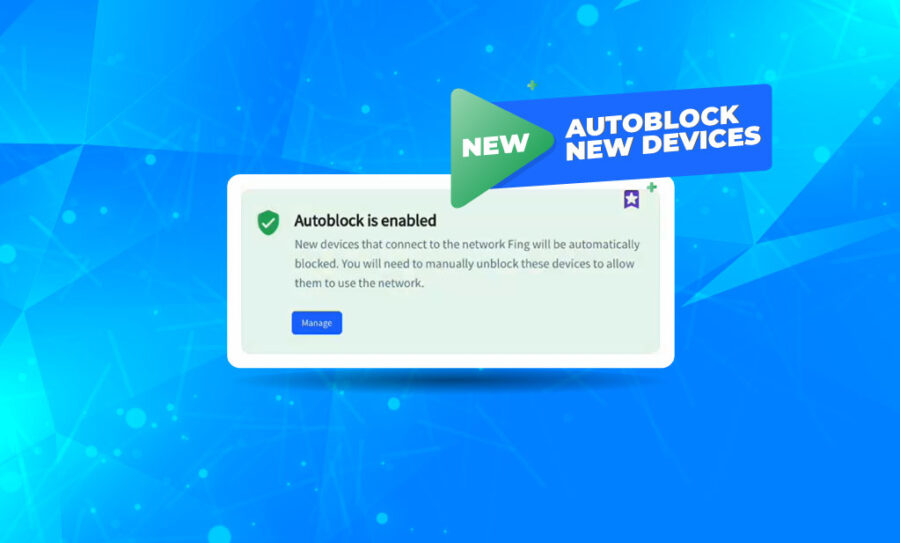
Fing Desktop 3.3: Introducing Auto Block for Unknown Devices
Since its initial release last February, the Block & Limit Internet Time features have become the most popular among Fing users. Having the chance to block unwanted devices from the Wi-Fi or limit Internet access for selected ones is a game changer when coming to home network management. But we did not stop there. We are working to give you constant product updates and today we introduce Fing Desktop 3.3,...
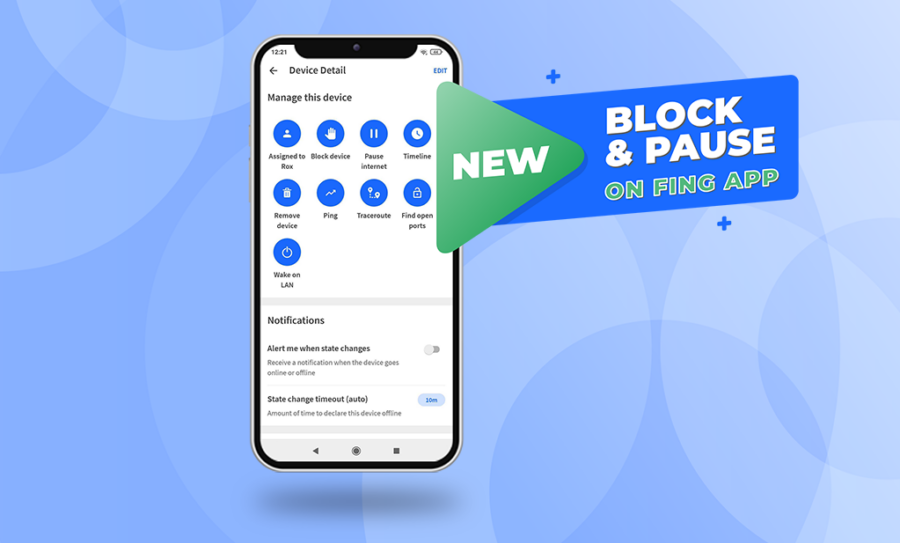
How to Restrict Internet Access Directly From Your Phone
And it’s live on mobile too! You read it correctly: the Block & Pause Preview is now also available on all mobile Fing apps. After first releasing the Block & Pause features on Fing Desktop, we are excited to announce you can monitor your network and restrict access to it directly from your phone, wherever you are. Let’s see how! Block & Pause Preview on mobile The Block & Pause...
The Dahua & Hikvision controversy: how it affects your network privacy
While Dahua and Hikvision products have been banned in the US over ethical and security concerns, many countries still make use of their surveillance technology. In February 2022, research by the Dutch national broadcasting company NOS revealed that these cameras are installed in over 50 municipalities in The Netherlands where the topic is trending. British media have shared similar data, stating that 60% of UK public bodies are using said...